Redshift Connection Guide
Requirements
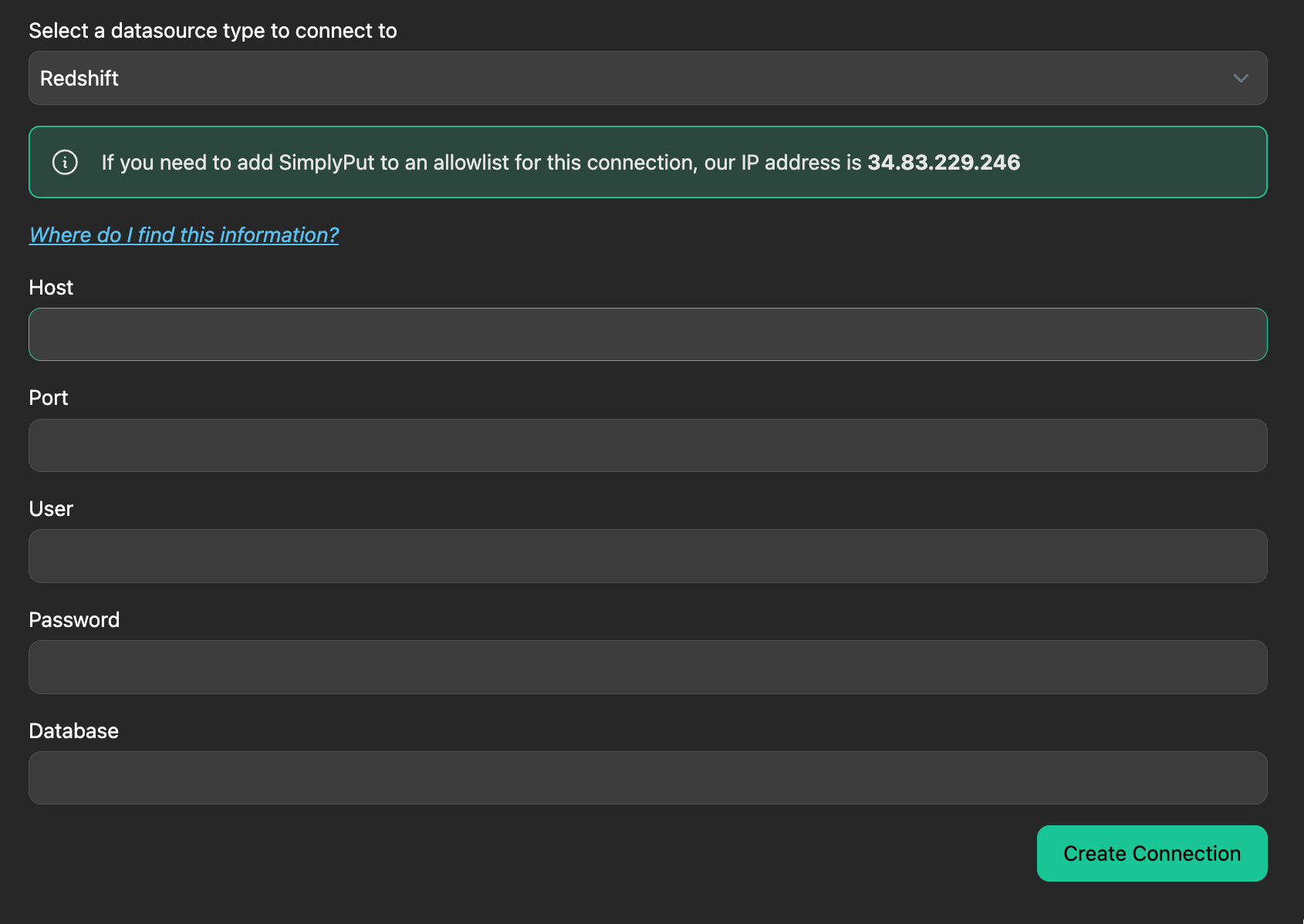
To connect Redshift with SimplyPut, you’ll need 5 main credentials:
- Host
- Port
- User
- Password
- Database
Locating the data source
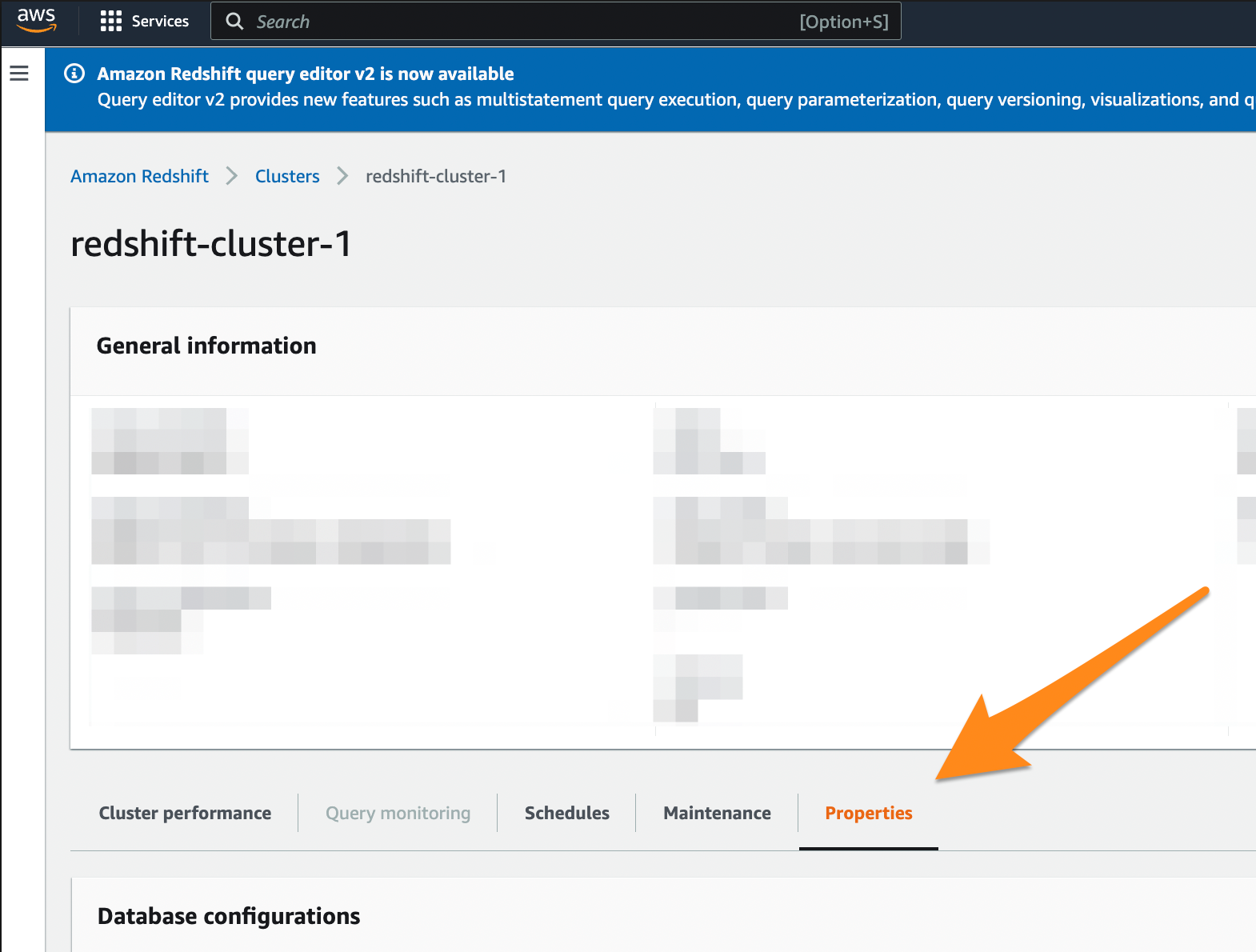
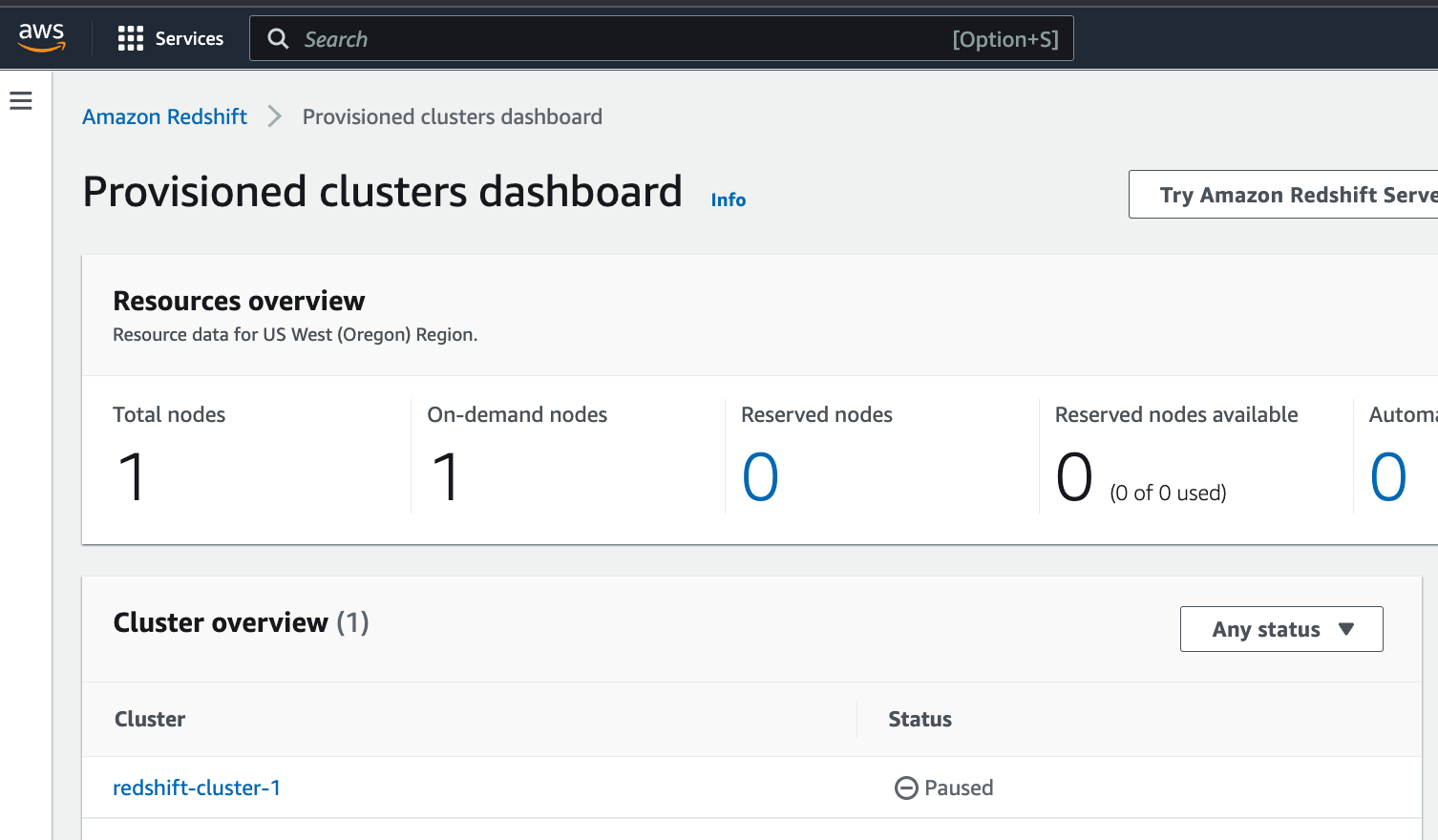
Go to your Amazon Redshift dashboard.
Select the cluster containing the data you wish to connect with SimplyPut. In this example, we are choosing redshift-cluster-1. Select the cluster containing the data you wish to connect with SimplyPut. In the example below, we are choosing redshift-cluster-1.
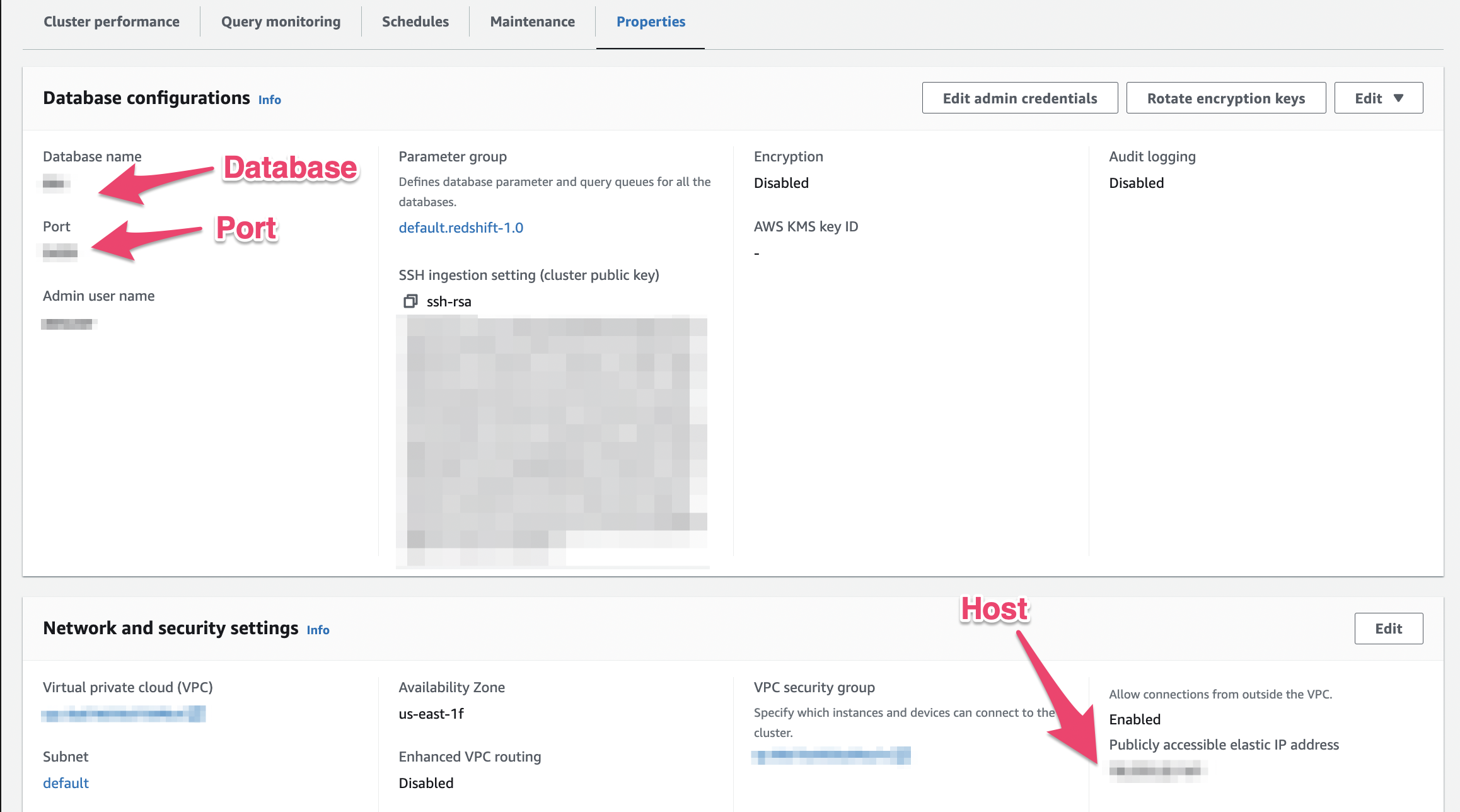
Host, Port, and Database
These credentials can be found in this tab as shown here.
Note: Make sure your host is publicly accessible.
User and Password:
Create a new user in Redshift and grant select access to your chosen Database
and Schema(s). To set up the necessary credentials, execute the following
SQL commands:
To set up the necessary credentials, execute the following SQL commands: sql
To set up the necessary credentials, execute the following SQL commands:
-- Create a new role
CREATE GROUP sp_role;
-- Create a new user and assign it to the role
CREATE USER sp_user PASSWORD '[password you choose]' IN GROUP sp_role;
-- Grant USAGE privilege on schema(s) (e.g., public)
GRANT USAGE ON SCHEMA [your schema] TO GROUP sp_role;
GRANT USAGE ON SCHEMA information_schema TO GROUP sp_role;
-- Grant SELECT privilege on all tables in the schema
GRANT SELECT ON ALL TABLES IN SCHEMA [your schema] TO GROUP sp_role;
GRANT SELECT ON ALL TABLES IN SCHEMA information_schema TO GROUP sp_role;
-- Grant SELECT privilege on all views in the schema
GRANT SELECT ON ALL VIEWS IN SCHEMA [your schema] TO GROUP sp_role;
GRANT SELECT ON ALL VIEWS IN SCHEMA information_schema TO GROUP sp_role;
-- Grant privileges on future tables
ALTER DEFAULT PRIVILEGES IN SCHEMA [your schema] GRANT SELECT ON TABLES TO GROUP sp_role;
ALTER DEFAULT PRIVILEGES IN SCHEMA information_schema GRANT SELECT ON TABLES TO GROUP sp_role;
-- Grant privileges on future views
ALTER DEFAULT PRIVILEGES IN SCHEMA [your schema] GRANT SELECT ON VIEWS TO GROUP sp_role;
ALTER DEFAULT PRIVILEGES IN SCHEMA information_schema GRANT SELECT ON VIEWS TO GROUP sp_role;